Managing devices in 2026 no longer means sending commands and hoping endpoints respond correctly. Across Apple, Android, and Windows ecosystems, device management has shifted toward declarative, autonomous, and AI‑driven models that fundamentally change how fleets are secured and operated.
For IT leaders and gadget enthusiasts alike, this transformation is more than incremental. Apple’s Declarative Device Management now lets devices maintain their own desired state, Android 16 integrates on‑device AI for real‑time anomaly detection, and Windows Autopilot enforces security updates before users even reach the desktop.
At the same time, zero‑touch deployment, autonomous endpoint management tools, and the transition to post‑quantum cryptography are reshaping enterprise security architecture. In this article, you will discover how these technologies connect, why they matter globally, and what they signal about the future of intelligent device ecosystems.
- Why 2026 Marks a Paradigm Shift in Mobile Device Management
- From Command-Based MDM to Declarative Device Management (DDM)
- Inside Apple’s DDM Architecture: Configurations, Assets, Activations, and Status Channels
- Android 16 and the Rise of Multi-Form-Factor Enterprise Computing
- On-Device AI with Gemini Nano: Autonomous Threat Detection at the Edge
- Windows Autopilot in 2026: Secure-by-Default Provisioning and Forced Quality Updates
- Unified Endpoint Management and Enterprise App Catalog Integration
- Autonomous Endpoint Management (AEM): Self-Healing Fleets at Scale
- Zero-Touch Deployment and Identity-Driven Provisioning Workflows
- Japan’s Explosive MDM Market Growth and the Impact of GIGA 2.0
- Compliance, BYOD Containerization, and Identity Threat Detection in 2026
- Preparing for Q-Day: Post-Quantum Cryptography and Cryptographic Agility in MDM
- 参考文献
Why 2026 Marks a Paradigm Shift in Mobile Device Management
In 2026, mobile device management no longer revolves around administrators pushing commands one by one. It shifts decisively toward a declarative, autonomous model in which devices maintain their own desired state and report meaningful changes in real time. This architectural transition redefines what “management” actually means.
Three structural forces drive this shift: the permanence of hybrid work, the surge in AI-driven automation, and the urgency of post-quantum security readiness. According to guidance from Apple, Microsoft, Google, and NIST, endpoint control is now expected to be resilient, self-correcting, and cryptographically agile by design.
Apple’s Declarative Device Management (DDM), fully matured in iOS 26 and macOS 17, exemplifies this transformation. Instead of polling thousands of devices for status, the server defines a desired state in structured declarations, and each device enforces and maintains that state locally. As Apple’s deployment documentation explains, devices proactively push status updates only when meaningful changes occur.
This reactive architecture eliminates the traditional bottleneck of serial command execution. Large fleets can now maintain near real-time inventory accuracy with dramatically reduced network overhead. Devices returning from offline states automatically reconcile drift before reporting compliance.
| Model | Control Logic | Operational Impact |
|---|---|---|
| Command-based MDM | Server issues sequential instructions | High polling traffic, delayed visibility |
| Declarative MDM | Device enforces declared desired state | Real-time reporting, autonomous remediation |
Android 16 advances the paradigm further by embedding on-device AI through Gemini Nano and AICore. Rather than waiting for cloud-side pattern analysis, endpoints perform anomaly detection locally, monitoring behavioral signals such as app usage patterns and communication domains. When risk is detected, work profiles can lock automatically without awaiting central instructions.
This edge-side intelligence shortens response time against zero-day threats while enhancing privacy, since sensitive telemetry remains on-device. Industry roadmaps from Android Enterprise emphasize identity-first deployment and least-privilege governance as foundational for this AI-assisted control layer.
On the Windows side, Microsoft’s 2026 updates to Autopilot enforce quality updates during the out-of-box experience. Devices now apply the latest monthly security patches before a user even reaches the desktop. Combined with Intune’s integration into Enterprise App Management and AI-monitored update rings, the system approaches secure-by-default provisioning at scale.
The shift is not purely architectural; it is also cryptographic. NIST’s standardization of post-quantum algorithms such as ML-KEM and ML-DSA has accelerated integration into operating systems and network stacks. Hybrid key exchange in TLS 1.3 and VPN protocols signals that endpoint management channels must now anticipate “harvest now, decrypt later” threats.
Cryptographic agility becomes a selection criterion for MDM platforms in 2026. Organizations are no longer evaluating tools solely on device enrollment features but on their ability to transition algorithms without hardware replacement.
Market dynamics reinforce the shift. In Japan, the MDM market is projected to grow at a CAGR exceeding 24%, driven by GIGA 2.0 refresh cycles and stricter privacy compliance standards. Under revised privacy frameworks, MDM logs serve as legal evidence of data separation in BYOD environments, elevating management from operational tooling to compliance infrastructure.
Finally, autonomous endpoint management platforms extend the concept beyond policy enforcement. Tools highlighted in 2026 industry comparisons demonstrate self-healing capabilities, automatically reattempting failed patches or rolling back unstable updates. This reduces manual ticket loads and reallocates IT resources toward governance and risk modeling.
Taken together, 2026 represents a clear inflection point. Devices think, enforce, and defend locally. Management platforms orchestrate rather than micromanage. Security models anticipate quantum-era threats. The paradigm shift is not incremental—it is structural, embedding autonomy and resilience into the very fabric of endpoint management.
From Command-Based MDM to Declarative Device Management (DDM)
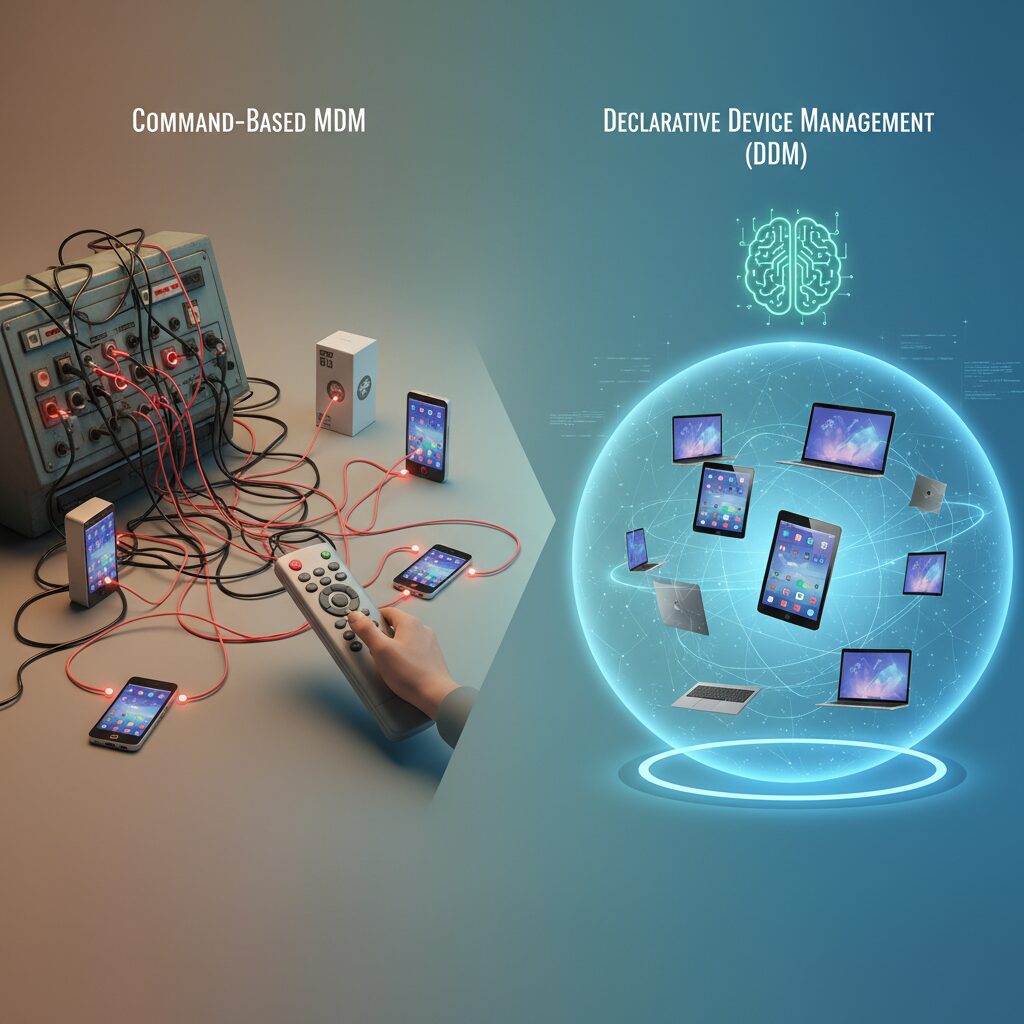
For more than a decade, traditional MDM operated on a simple premise: the server commands, the device obeys. This command-based model relied on sequential instructions such as installing an app or enforcing a passcode, with the server polling devices to confirm compliance.
In 2026, that paradigm has fundamentally shifted. With the maturation of Apple’s Declarative Device Management (DDM) in iOS 26 and macOS 17, endpoint management is no longer about issuing endless commands, but about defining intent and letting devices enforce it autonomously.
This transition from command-driven control to state-driven autonomy is redefining scalability, resilience, and real-time visibility in enterprise IT.
Command-Based vs. Declarative Architecture
| Aspect | Command-Based MDM | Declarative Device Management |
|---|---|---|
| Control Logic | Server issues step-by-step commands | Server defines desired state |
| Communication Model | Polling and response cycles | Event-driven status updates |
| Scalability | Server bottlenecks at scale | Device-side evaluation reduces load |
| Offline Behavior | Limited until reconnect | Local enforcement continues offline |
Under the legacy model, administrators had to wait for each instruction to execute before moving to the next. In large fleets, this created latency and heavy network traffic, especially when querying inventory data across thousands of endpoints.
DDM replaces that bottleneck with a declarative data model. Instead of transmitting individual commands, the server sends a structured declaration describing the desired configuration state in JSON format. The device evaluates that declaration locally and takes the necessary actions to achieve and maintain compliance.
According to Apple’s enterprise deployment documentation, this device-driven evaluation significantly reduces round trips between server and endpoint, enabling near real-time state alignment without constant polling.
A critical innovation is the status channel. Rather than waiting to be asked, devices proactively report meaningful changes such as OS updates, configuration drift, or compliance violations.
This event-driven reporting model transforms visibility. Administrators no longer need to query “What version are you running?” across the fleet. Devices notify the management service only when something changes, dramatically reducing unnecessary traffic.
The result is a shift from reactive oversight to continuous, autonomous compliance assurance.
Another structural advantage lies in conditional activations. Declarative logic allows policies to be dynamically enabled or disabled based on context, such as network conditions or time constraints, without issuing new commands each time.
This contextual awareness means the intelligence resides on the device itself. Even if temporarily offline, it can reconcile its current state against the declared baseline and self-correct once conditions are met.
Industry analysts such as Esper have highlighted that this architecture moves enforcement closer to the edge, aligning device management with broader trends in distributed computing and zero-trust security.
Ultimately, the transition to DDM is not just a protocol upgrade. It represents a philosophical shift in endpoint governance. Administrators define intent, compliance thresholds, and structural guardrails, while devices assume responsibility for maintaining alignment.
In an era of hybrid work and exploding endpoint counts, this declarative model provides the technical foundation for managing tens of thousands of devices without proportional increases in infrastructure or staffing.
From centralized command execution to autonomous state convergence, device management has entered a new operational era.
Inside Apple’s DDM Architecture: Configurations, Assets, Activations, and Status Channels
Apple’s Declarative Device Management (DDM) is built on a data-driven architecture that shifts intelligence from the server to the device. Instead of sending one command at a time, the management server delivers a set of structured declarations describing the desired state. The device evaluates, applies, and maintains that state locally.
This architecture is composed of four tightly integrated declaration types: Configurations, Assets, Activations, and Management. According to Apple’s deployment documentation and technical sessions for developers, these components form a modular data model that allows scalable and reactive management across iOS 26 and macOS 17 environments.
| Declaration Type | Primary Role | Device Responsibility |
|---|---|---|
| Configurations | Define settings, restrictions, accounts | Enforce and maintain compliance |
| Assets | Provide supporting data via URL | Fetch and cache securely |
| Activations | Set logical conditions for enforcement | Evaluate predicates locally |
| Management | Describe organizational authority | Align with assigned MDM service |
Configurations function as the core policy layer. They resemble traditional MDM profiles but offer finer granularity and are interpreted declaratively. For example, advanced passcode rules or Wi‑Fi constraints tied to specific SSIDs are described as state definitions rather than sequential commands. The device continuously ensures alignment with those definitions without repeated server polling.
Assets complement configurations by externalizing heavy or variable data. Apple’s developer documentation explains that assets can be referenced via URLs and retrieved from content delivery networks. This design enables distribution of large certificates, branding elements, or training media without bloating the core declaration payload.
Activations introduce contextual intelligence. They define logical predicates such as time conditions or network context. Because evaluation occurs on-device, enforcement becomes instantaneous. A policy can activate or deactivate based on real-time state changes, eliminating latency that was inherent in server-driven models.
Management declarations clarify organizational metadata and service authority. This ensures that devices understand which management service governs them and allows seamless transitions during server migration scenarios. It reduces ambiguity and strengthens trust boundaries within enterprise fleets.
Status Channels complete the architecture. Instead of waiting for queries, devices proactively send state updates when meaningful changes occur. Industry analyses such as those from Esper and Addigy note that this delta-based reporting dramatically reduces network overhead while improving accuracy.
When an OS update completes or a compliance condition changes, the device pushes structured status information immediately. In large-scale deployments of tens of thousands of endpoints, this reactive reporting model enables near real-time inventory visibility without constant polling traffic.
Offline resilience is another critical advantage. Devices maintain a local representation of the declared desired state. If connectivity is interrupted, enforcement continues autonomously. Once reconnected, only differential status data is transmitted, preserving both bandwidth and management continuity.
For technically inclined readers, DDM’s architecture represents more than efficiency gains. It reflects a fundamental redefinition of control logic in endpoint management. **Intent is centralized, but enforcement is decentralized**, creating a scalable system that aligns with the realities of distributed workforces and increasingly autonomous devices.
Android 16 and the Rise of Multi-Form-Factor Enterprise Computing

Android 16 marks a decisive shift from smartphone-centric management to a truly multi-form-factor enterprise model. Devices are no longer treated as isolated endpoints but as adaptive compute nodes that fluidly transition between phone, tablet, foldable, and desktop contexts. According to the 2026 Android roadmap discussions within the Android Enterprise community, IT teams are now expected to govern productivity environments that rival traditional PCs in both capability and risk surface.
This evolution transforms Android Enterprise from mobile management into distributed workspace orchestration. When a single device can dock into an external monitor, resize apps in freeform windows, and support drag-and-drop workflows, policy design must account for spatial computing behaviors rather than just app permissions.
From Mobile Profiles to Context-Aware Workspaces
Android 16 standardizes desktop windowing, advanced multitasking, and large-screen optimization. For enterprises, this means policies must dynamically adapt to display mode, input method, and network state. A device connected to a corporate LAN via Ethernet in desktop mode presents a different exposure profile than the same device on public Wi-Fi in handheld mode.
| Form Factor | Enterprise Use Case | Management Priority |
|---|---|---|
| Smartphone | Field operations, secure messaging | Work profile isolation |
| Foldable | Mobile presentations, multitasking | App continuity control |
| Desktop Mode | PC replacement scenarios | Clipboard and external display governance |
The introduction of refined WindowInsets handling and edge-to-edge defaults also affects enterprise apps. Management agents must ensure administrative overlays and compliance notifications remain visible without interfering with system UI elements. This subtle UI governance becomes critical in regulated industries where proof-of-policy visibility matters.
On-Device AI as a Security Multiplier
Another defining pillar is the integration of Gemini Nano through AICore. Unlike legacy cloud-dependent monitoring, Android 16 devices analyze behavioral signals locally. Typing cadence, app launch frequency, and domain access patterns are evaluated on-device, enabling near-instant containment actions.
Industry analysis referenced in Android’s 2026 platform outlook highlights that edge-based anomaly detection significantly reduces response latency compared to server-triggered enforcement. When suspicious behavior emerges, the work profile can be locked before data exfiltration occurs, without transmitting raw behavioral data to the cloud.
This architecture also strengthens privacy compliance. Because inference occurs locally, organizations can align with stricter data protection frameworks while still maintaining high assurance controls. For multinational enterprises balancing regional regulations, this local-first intelligence model becomes strategically valuable.
Ultimately, Android 16 positions the device as both productivity engine and policy executor. IT departments are no longer managing “phones” but governing adaptive computing environments that expand and contract with user context. In the era of hybrid work and AI-native endpoints, multi-form-factor enterprise computing is not an enhancement—it is the new operational baseline.
On-Device AI with Gemini Nano: Autonomous Threat Detection at the Edge
In 2026, Android 16 fundamentally redefines endpoint security by embedding Gemini Nano directly on the device, enabling autonomous threat detection without constant cloud dependence. This architectural shift moves security intelligence from centralized analysis to the edge, where decisions are executed in real time.
Unlike traditional MDM models that rely on server-side pattern matching, on-device AI continuously evaluates behavioral signals locally. According to Google’s 2026 Android roadmap disclosures, Gemini Nano operates through AICore to process contextual data without exporting raw user information, significantly reducing privacy exposure.
The result is immediate, privacy-preserving defense that does not wait for external validation.
Edge-Based Behavioral Analysis
Gemini Nano analyzes multiple behavioral vectors simultaneously, forming a dynamic trust model of the user and device state. Rather than scanning static signatures, it detects deviations from established behavioral baselines.
| Signal Category | Analyzed Locally | Security Impact |
|---|---|---|
| Typing Patterns | Keystroke rhythm and cadence | Account takeover detection |
| App Usage Behavior | Launch frequency and sequence | Insider threat anomaly detection |
| Network Destinations | Domain reputation shifts | Zero-day phishing mitigation |
If anomalous activity crosses predefined risk thresholds, the device does not wait for an administrator’s command. It can immediately lock the work profile or restrict sensitive data access, dramatically shortening response latency compared to cloud-triggered enforcement.
This approach aligns with broader autonomous endpoint management trends highlighted in 2026 industry analyses, where self-healing and self-defending capabilities are becoming standard expectations rather than premium add-ons.
Privacy-First Security Architecture
One of the most critical advantages of on-device AI is data minimization. Because inference occurs locally, sensitive telemetry does not need to be transmitted for central inspection. This design directly addresses regulatory pressures around data sovereignty and personal information handling.
Processing at the edge means fewer opportunities for interception, exfiltration, or retrospective decryption. In a landscape increasingly concerned with “harvest now, decrypt later” risks discussed by NIST in its post-quantum transition guidance, limiting transmitted data becomes a strategic security layer in itself.
For enterprises deploying Android at scale, this translates into measurable operational benefits: reduced network load, lower SIEM ingestion costs, and faster containment of compromised sessions.
For security teams managing thousands of distributed devices across hybrid work environments, autonomous threat detection at the edge eliminates dependency on constant connectivity. Even offline devices retain defensive intelligence, maintaining policy integrity until full synchronization resumes.
In practical terms, Gemini Nano does not replace centralized MDM oversight. Instead, it augments it with localized decision-making, ensuring that protection occurs at the exact moment risk emerges.
This fusion of AI inference and device-level enforcement marks a decisive shift toward truly autonomous endpoint security.
Windows Autopilot in 2026: Secure-by-Default Provisioning and Forced Quality Updates
In 2026, Windows Autopilot has moved beyond simple zero-touch deployment and into a secure-by-default provisioning model. The biggest shift is what happens during the Out-of-Box Experience (OOBE), before a user ever reaches the desktop.
According to Microsoft Learn, starting with the January 2026 Windows quality update (2026-01 B), devices provisioned with Autopilot automatically install the latest monthly quality updates during OOBE when the Install Windows quality updates setting is enabled by default. This means a device is no longer “fresh from the factory” but potentially vulnerable on day one.
The OS is brought to a secure baseline before user productivity begins. For security-conscious organizations, this closes the historic gap between manufacturing and first login.
OOBE Security Enforcement Flow
| Stage | What Happens | Security Impact |
|---|---|---|
| Device boots | Autopilot profile retrieved from cloud | Policy-bound setup begins immediately |
| OOBE phase | Latest monthly quality update installed | Mitigates newly disclosed vulnerabilities |
| Enrollment Status Page | Blocking apps enforced | Prevents user access until critical agents install |
This enforced update model is particularly important in hybrid work environments, where devices may ship directly to remote employees. Without this mechanism, systems could remain exposed to vulnerabilities discovered after imaging but before delivery.
Autopilot’s Enrollment Status Page (ESP) further strengthens this posture. Administrators can define security agents such as EDR tools as blocking applications, ensuring that users cannot access the desktop until those protections are fully deployed. This effectively transforms provisioning into a controlled security gate rather than a convenience workflow.
Microsoft has also hardened the infrastructure behind the scenes. As documented in recent Autopilot updates, newer Intune Connector builds transition authentication components to WebView2, reducing legacy browser-based attack surfaces. Additionally, low-privilege operational models for hybrid Entra ID and Active Directory environments reduce credential exposure during enrollment.
The result is a measurable reduction in first-day risk. Devices are patched, identity-bound, and security-instrumented before productivity begins.
For enterprises managing thousands of endpoints, this model changes procurement and rollout strategy. Hardware staging centers no longer need to pre-patch images manually, and compliance teams gain assurance that every Autopilot-enrolled device meets a defined security baseline from its first active minute.
In 2026, Windows Autopilot is not just about automation. It is about enforcing security posture at the earliest possible control point—before the user ever clicks Start.
Unified Endpoint Management and Enterprise App Catalog Integration
Unified Endpoint Management (UEM) in 2026 is no longer just about consolidating consoles. It is about orchestrating declarative, AI-assisted, and zero-touch mechanisms across Apple, Android, and Windows into a single governance layer that continuously enforces desired state.
As hybrid work has permanently expanded the number and diversity of endpoints, organizations require a model where device posture, identity, and application lifecycle are evaluated together. According to Microsoft Learn, recent enhancements in Windows Autopilot and Intune emphasize secure-by-default provisioning tightly coupled with policy enforcement during setup.
The strategic shift is from device-centric control to policy-centric orchestration across platforms.
| Layer | Role in UEM | 2026 Evolution |
|---|---|---|
| Device Management | Enforces configurations and compliance | Declarative models such as Apple DDM reduce server polling |
| Identity Integration | Binds user context to device state | Entra ID–driven conditional access during Autopilot enrollment |
| Enterprise App Catalog | Standardizes trusted app distribution | Pre-validated packages via Intune Enterprise App Catalog |
The integration of Enterprise App Catalog capabilities into UEM platforms significantly reduces operational overhead. In Microsoft Intune, administrators can deploy thousands of curated enterprise applications without custom packaging. This eliminates a traditional bottleneck in software distribution and minimizes human error during MSI or Win32 wrapping.
More importantly, these catalog apps can be designated as blocking apps within the Enrollment Status Page. This means security agents such as EDR tools must install successfully before the user gains desktop access. Security enforcement therefore shifts left, into the provisioning phase itself.
This model aligns with zero-touch deployment best practices described in industry guidance for 2026, where devices ship directly to employees and automatically enroll through identity-driven workflows. When a user signs in with Entra ID, role attributes determine which catalog apps are installed, creating dynamic, department-aware provisioning.
Apple’s declarative device management complements this by allowing configurations and assets to persist locally on the device, while status channels report compliance changes in real time. Android Enterprise’s roadmap similarly emphasizes identity foundation and least-privilege administration, reinforcing cross-platform alignment.
UEM becomes the control plane, while enterprise app catalogs become the trust layer. Together, they ensure that only validated software enters the environment and that it remains continuously compliant with evolving policy.
For advanced organizations, the next step is combining catalog distribution with autonomous endpoint management features. AI-driven monitoring tools can detect installation failures or drift and automatically retry or remediate, preserving patch compliance targets without manual intervention.
In 2026, successful endpoint strategy depends on how tightly UEM integrates identity, declarative policy, and curated application supply chains. Enterprises that treat app distribution as a governed pipeline rather than a deployment task achieve stronger security posture, lower operational cost, and faster employee onboarding.
Autonomous Endpoint Management (AEM): Self-Healing Fleets at Scale
Autonomous Endpoint Management (AEM) represents the next logical step beyond traditional MDM and even unified endpoint management. Instead of waiting for administrators to investigate alerts, AEM platforms continuously detect, decide, and remediate issues on their own. This shift is driven by a structural reality: endpoint fleets have grown faster than IT headcount.
According to Atera’s 2026 industry analysis, leading AEM tools now resolve up to 40% of IT tickets autonomously through AI-driven workflows. This is not simple automation based on static scripts. It is policy-aware, context-sensitive execution that adapts to device state, user behavior, and historical telemetry.
The architectural difference becomes clear when comparing legacy management with self-healing models.
| Model | Trigger | Remediation Logic | Human Involvement |
|---|---|---|---|
| Reactive IT | User ticket | Manual troubleshooting | High |
| Scripted Automation | Predefined alert | Static script | Medium |
| AEM | Real-time telemetry | AI-driven, adaptive | Minimal |
At the core of AEM is continuous telemetry ingestion. Platforms such as Tanium AEM collect real-time signals across millions of heterogeneous endpoints, enabling immediate detection of drift, missing patches, or abnormal configurations. When deviation from a defined compliance threshold occurs, the system initiates corrective actions without waiting for approval cycles.
Microsoft Intune combined with Autopatch demonstrates this principle in patch governance. AI monitors update rings and, if instability is detected, automatically pauses or rolls back deployments. This dynamic rollback capability dramatically reduces blast radius compared to traditional staged rollouts.
Ivanti Neurons extends the concept into predictive remediation. By analyzing historical incident patterns, it can identify devices likely to fail compliance before the user experiences disruption. The system then preemptively applies patches or configuration fixes. This predictive layer transforms endpoint management from firefighting into risk anticipation.
Scalability is where AEM proves its strategic value. In environments managing tens or hundreds of thousands of endpoints, even a 10% reduction in manual tickets translates into substantial operational savings. More importantly, it reallocates skilled IT staff toward architecture design, security governance, and cryptographic agility planning.
For gadget-focused organizations deploying diverse device types, AEM also bridges OS fragmentation. By abstracting remediation logic from specific platforms, enterprises maintain consistent security posture across Windows, macOS, Android, and mixed environments.
In 2026, endpoint management is no longer about issuing commands. It is about engineering autonomous systems that maintain equilibrium at scale, report deviations instantly, and repair themselves before disruption spreads.
Zero-Touch Deployment and Identity-Driven Provisioning Workflows
Zero-Touch Deployment has reached a level of maturity in 2026 where IT teams no longer image, configure, or even physically handle devices before they reach end users. Instead, identity becomes the trigger that activates configuration, security posture, and application delivery. The device ships directly from distributor to employee, and everything else is orchestrated through cloud-based management and federation with Identity Providers.
The defining shift is that provisioning now begins with who the user is, not what the device is. As Microsoft Learn documentation on Windows Autopilot explains, devices are pre-registered by hardware ID, and policies are assigned before first boot. When the user authenticates with Entra ID, the enrollment and configuration sequence is automatically initiated without IT-side touchpoints.
Identity-Driven Provisioning Flow
| Phase | Trigger | Automated Outcome |
|---|---|---|
| Pre-registration | Reseller uploads device ID | Device linked to tenant and profile |
| First Boot (OOBE) | User signs in via IdP | Automatic MDM enrollment |
| Role Evaluation | Directory attributes | Apps and policies assigned dynamically |
| Post-Setup Compliance | Status signals from device | Continuous drift correction |
Research and vendor guidance in 2026 emphasize tight coupling between IdP platforms such as Entra ID or Okta and MDM systems. According to enterprise deployment guides from Omnissa and BlackBerry UEM documentation, attribute-based access control enables devices to inherit configurations automatically based on department, location, or risk score. This eliminates static imaging models and reduces configuration errors caused by manual grouping.
Security is embedded into the onboarding pipeline itself. With Windows Autopilot’s enforced quality updates during OOBE, devices apply the latest security patches before the desktop becomes accessible. Critical security agents can be designated as blocking applications, ensuring endpoint protection is active before productive use begins. This transforms onboarding from a convenience feature into a secure-by-default control mechanism.
In Apple ecosystems leveraging declarative management, the device evaluates its desired state locally once enrolled. Combined with identity-driven assignment, this reduces server-side orchestration overhead and allows thousands of endpoints to be provisioned simultaneously without traffic spikes. Android Enterprise similarly integrates zero-touch enrollment with Managed Google Domains, aligning account identity with work profile creation at first activation.
From an operational standpoint, the impact is measurable. Autonomous endpoint management vendors report significant reductions in ticket volume when identity-based provisioning replaces manual setup workflows. Because policies follow the user rather than the hardware, role changes automatically reconfigure access rights, minimizing privilege creep and audit gaps.
In hybrid and remote-first environments, this model ensures that the first secure state is established regardless of geography. A developer in Tokyo, a sales executive in Berlin, or a contractor in Toronto all receive context-aware configurations within minutes of powering on a sealed device. The physical supply chain and the digital identity layer converge, creating a provisioning workflow that is scalable, secure, and resilient by design.
Japan’s Explosive MDM Market Growth and the Impact of GIGA 2.0
Japan’s mobile device management market is entering an explosive growth phase, and the catalyst is unmistakable: large-scale public policy combined with structural digital transformation.
According to market analyses cited by IMARC and other industry reports, Japan’s MDM market is projected to grow at a CAGR of 24.06%, expanding from approximately USD 601.1 million in 2025 to over USD 4.18 billion by 2034. This pace significantly outstrips many mature IT segments in the country.
This is not incremental growth driven by corporate refresh cycles. It is a policy-driven, compliance-driven, and education-driven expansion.
| Metric | Value | Source Context |
|---|---|---|
| Market size (2025) | USD 601.1M | Japan MDM industry report |
| Forecast (2034) | USD 4.18B | Long-term growth projection |
| CAGR | 24.06% | 2025–2034 estimate |
The single most powerful accelerant is GIGA School Program Phase 2, commonly referred to as GIGA 2.0. Following the initial nationwide deployment of one device per student, Japan is now entering a concentrated refresh cycle.
Data from MM Research Institute shows that 68% of replacement demand is concentrated in fiscal year 2025, with an additional 21% continuing into fiscal year 2026. That translates into millions of devices being re-evaluated, re-procured, and re-managed within an extremely tight window.
Every refresh is not just a hardware decision. It is an MDM decision.
Notably, 57% of municipalities that have finalized their refresh direction are choosing ChromeOS. This has direct implications for centralized, cloud-native device management via Google Admin Console, reinforcing demand for scalable policy orchestration rather than traditional on-premises control models.
At the same time, 48% of municipalities express concern about budget constraints due to yen depreciation and rising PC prices, also reported by MM Research Institute. This economic pressure shifts purchasing criteria toward:
Cost-efficient MDM licensing models, multi-year supply guarantees, and simplified large-scale provisioning capabilities.
In practical terms, education-driven scale forces vendors to optimize for:
High-volume zero-touch enrollment, automated policy inheritance at the classroom or grade level, and low-bandwidth update strategies suitable for regional infrastructure disparities.
Vendors that cannot operate efficiently at the scale of tens or hundreds of thousands of endpoints per prefecture are effectively excluded.
The impact extends beyond education. The revised PrivacyMark standards, fully transitioned in January 2026, elevate MDM from an operational IT tool to a compliance instrument. As NTT East’s business commentary on the new P-Mark framework explains, organizations must now demonstrate concrete technical controls over personal data handling.
In BYOD scenarios, this means provable separation between personal and corporate domains, auditable logs, and conditional access enforcement tied to device posture.
MDM logs are increasingly treated as regulatory evidence, not just administrative telemetry.
Additionally, cybersecurity trend analyses in Japan highlight identity-linked device trust and ITDR adoption as priority areas in 2026. This reinforces conditional access architectures where device compliance status directly governs authentication rights.
As a result, Japan’s MDM surge is structurally different from simple digitization waves seen in the past decade.
It is driven simultaneously by public education infrastructure, compliance modernization, security hardening, and macroeconomic constraints—creating a uniquely intense, policy-synchronized expansion cycle.
For vendors and enterprise IT leaders, GIGA 2.0 is not merely a renewal program. It is a stress test of scalability, cost architecture, and governance maturity in one of the world’s most regulation-conscious technology markets.
Compliance, BYOD Containerization, and Identity Threat Detection in 2026
In 2026, compliance is no longer a static checklist but a continuously evaluated state tied directly to device posture and identity signals.
With declarative management models such as Apple’s DDM and AI-driven endpoint analytics on Android and Windows, endpoints now report their status proactively, enabling near real-time compliance validation.
This shift has fundamentally changed how organizations approach BYOD, containerization, and Identity Threat Detection and Response (ITDR).
In Japan, the revised PrivacyMark standards fully enforced in January 2026 have elevated technical separation of personal and corporate data from a best practice to a quasi-mandatory requirement.
According to NTT East’s compliance commentary on the updated criteria, organizations must demonstrate not only policy intent but also technical evidence that personal information is appropriately segregated and controlled.
MDM audit logs and configuration reports are increasingly used as proof during certification reviews.
| Area | 2026 Compliance Expectation | Technical Mechanism |
|---|---|---|
| BYOD | Clear separation of personal and work data | Work profiles, managed containers |
| Data Access | Conditional access based on device health | Real-time posture reporting (DDM, Intune) |
| Identity Security | Detection of account takeover and insider risk | On-device AI + ITDR platforms |
On Android Enterprise, work profiles continue to be the cornerstone of BYOD deployments.
Android 16 enhances this model by integrating on-device AI (Gemini Nano) capable of detecting anomalous behavior patterns locally.
If suspicious activity is detected, the system can automatically lock the work profile without exposing personal data, reinforcing privacy by design.
Apple’s declarative approach strengthens compliance in a different way.
Because devices maintain and self-correct toward a defined “desired state,” configuration drift in BYOD scenarios is reduced dramatically.
Compliance is enforced as a condition of access, not as a periodic audit event.
Identity Threat Detection and Response has become tightly coupled with device management.
As highlighted in 2026 cybersecurity trend analyses by major system integrators such as CTC, identity-based attacks now dominate breach vectors, particularly in hybrid work environments.
Modern ITDR correlates authentication signals, device compliance status, geolocation anomalies, and behavioral analytics before granting access.
For example, if an employee’s credentials are used from an unusual region while the device simultaneously reports a deviation from its security baseline, conditional access engines can enforce step-up authentication or block access entirely.
This dynamic enforcement model reflects the convergence of Zero Trust architecture and advanced endpoint telemetry.
It is no longer sufficient to trust either the user or the device independently.
Another notable trend in 2026 is the integration of ITDR with autonomous endpoint management platforms.
AI-driven systems can initiate remediation workflows automatically, such as revoking tokens, rotating credentials, or triggering remote isolation.
Response time is measured in seconds rather than hours, reducing the blast radius of credential-based attacks.
From a governance perspective, organizations are now required to document how identity, device posture, and encryption standards interoperate.
With post-quantum cryptography gradually being integrated into operating systems and network protocols, compliance teams must also verify cryptographic agility within MDM communications.
This ensures that both identity assertions and device management channels remain resilient against future decryption risks.
In 2026, compliance, BYOD containerization, and identity threat detection are no longer separate disciplines.
They form a unified trust framework where device autonomy, AI-based anomaly detection, and regulatory accountability intersect.
Organizations that treat these elements as an integrated control plane achieve stronger security without sacrificing user privacy or flexibility.
Preparing for Q-Day: Post-Quantum Cryptography and Cryptographic Agility in MDM
Q-Day, the moment when practical quantum computers can break today’s public‑key cryptography, is no longer a distant hypothesis. Security experts warn about the “Harvest Now, Decrypt Later” scenario, where encrypted MDM traffic is captured today and decrypted years later once quantum capability matures. In endpoint management, this risk is particularly acute because device enrollment records, certificates, and configuration payloads often retain long-term value.
According to NIST, the standardization of post-quantum cryptography (PQC) algorithms such as ML-KEM (formerly Kyber) for key establishment and ML-DSA (formerly Dilithium) for digital signatures marks a decisive transition phase. By 2026, these algorithms are being integrated into major operating systems and cryptographic libraries, enabling early production deployments in controlled environments.
In practical MDM scenarios, cryptography underpins three critical layers: device enrollment, policy distribution, and ongoing telemetry communication. If any of these channels rely solely on classical RSA or ECC without hybrid support, organizations risk long-term exposure.
| MDM Layer | Classical Dependency | PQC Transition Approach |
|---|---|---|
| Device Enrollment | Certificate-based TLS | Hybrid TLS 1.3 with ML-KEM |
| Policy Signing | RSA/ECDSA signatures | ML-DSA-based signature validation |
| Agent Communication | Standard key exchange | Hybrid key exchange with crypto agility |
Leading guidance, including transition roadmaps referenced by PQC specialists and NIST publications, emphasizes a phased migration. Hybrid cryptography, combining classical and post-quantum algorithms in the same handshake, is considered a best practice during 2026. This approach ensures backward compatibility while providing forward secrecy against quantum adversaries.
However, deploying PQC is only half of the equation. The more strategic capability is cryptographic agility. This means the MDM server, agents, and even firmware trust anchors are designed to swap algorithms through software updates rather than hardware replacement. In a world where algorithms may be deprecated as cryptanalysis evolves, static cryptographic design becomes a liability.
For example, if an enterprise deploys thousands of devices with hard-coded certificate validation logic, transitioning to a new signature scheme could require costly device recalls. By contrast, MDM platforms that abstract cryptographic functions into updateable modules allow administrators to rotate trust chains and update key exchange methods remotely.
Government timelines accelerate this urgency. Under initiatives such as CNSA 2.0 in the United States, new national security systems must become quantum-resistant within defined deadlines. Even private enterprises that operate in regulated industries will increasingly face procurement requirements demanding PQC readiness from their MDM vendors.
Preparing for Q-Day therefore involves three concrete actions in 2026: inventorying cryptographic dependencies across the MDM stack, validating vendor support for NIST-standardized PQC algorithms, and embedding crypto agility into procurement criteria. Organizations that treat post-quantum readiness as a firmware-level concern rather than a strategic architecture issue may find themselves locked into obsolete trust models.
MDM in the quantum era is no longer just about device control. It is about preserving the long-term confidentiality and integrity of every policy, credential, and telemetry stream that defines the enterprise’s digital nervous system.
参考文献
- Apple Support:Use declarative device management to manage Apple devices
- Esper:What Is Declarative Device Management?
- Microsoft Learn:What’s new in Windows Autopilot
- Android Enterprise and ChromeOS Customer Communities:What to Include in Your 2026 Plan: A Quarterly Roadmap to Maximize Your Android Deployment
- Atera:Top 10 autonomous endpoint management tools in 2026
- NIST:Post-quantum cryptography
- Workwize:Zero Touch Deployment: A Complete Guide for 2026
